

SAP security ensures that sensitive business and personal data in SAP systems is protected against unauthorized access, tampering, and loss. From role-based access control and encryption to advanced monitoring, SAP offers built-in safeguards and standalone solutions for compliance with global regulations like GDPR and HIPAA. Businesses can leverage tools such as SAP Identity Management, SAP GRC, and SAP Enterprise Threat Detection to secure both on-premise and cloud landscapes. A layered approach to security protects applications, data, and infrastructure across the SAP ecosystem.
SAP utilizes the following security concepts throughout its suites of products: segregation of duties, access control, cryptography, user management, data locking, multiple authorization roles, logging, user authentication, development testing such as ABAP debugging, field masking, UI logging, multi-factor authentication, role-based access control, data anonymization and pseudonymization, SSO, SSL, and SAML.
SAP also encourages complex password requirements and provides vulnerability and penetration testing, multiple encryption types, and monitoring. Additionally, SAP offers a whole host of security options for individual databases such as Oracle, Microsoft SQL, and SAP HANA.
SAP releases regular security patches to its solutions, on the second Tuesday of every month, to fix any new vulnerabilities unearthed.
SAP provides numerous business applications based on different architectures: NetWeaver AS ABAP and Java, BusinessObjects, SAP HANA, and cloud-based applications such as SAP SuccessFactors or SAP Ariba.
The first line of defense for each of these solutions are the system backends, where admins can implement security, define roles, create access requirements, and configure the concepts listed above. Additional security functionality exists within the solutions themselves as each has its own considerations. For example, cloud-based applications have different security needs than on-premise solutions, and SAP BTP applications have their own identity/authentication mechanisms integrated with SAP Identity Services.
Beyond basic system administration and solution-specific security, however, SAP offers multiple security-related products to be used in tandem with the existing functionality. Here are the key SAP security solutions.
SAP Cloud Identity Access Governance is a cloud-based tool for admins to use in simplifying governance processes. Functionality includes continuous access analysis, user assignment optimization, preconfigured audit reporting, and more. You can also connect it to on-premise SAP Access Control.
Also known as SAP NetWeaver AS Code Vulnerability Analysis (CVA), the SAP Code Vulnerability Analyzer is an ABAP add-on that analyzes source code and secures it from potential attacks before delivering applications to end users.
SAP Data Custodian is a solution for public cloud users to consult when looking for security information on their specific cloud, providing greater transparency and increased trust for those involved in the public cloud.
SAP Data Retention Manager is a solution for businesses to use to block or destroy personal data. It is used on SAP BTP apps.
This application is a joint venture between SAP and NextLabs, a data security software firm. SAP Dynamic Authorization Management provides secure collaboration tools so stakeholders across the business network can work together, regardless of whether they’re employed by the same company.
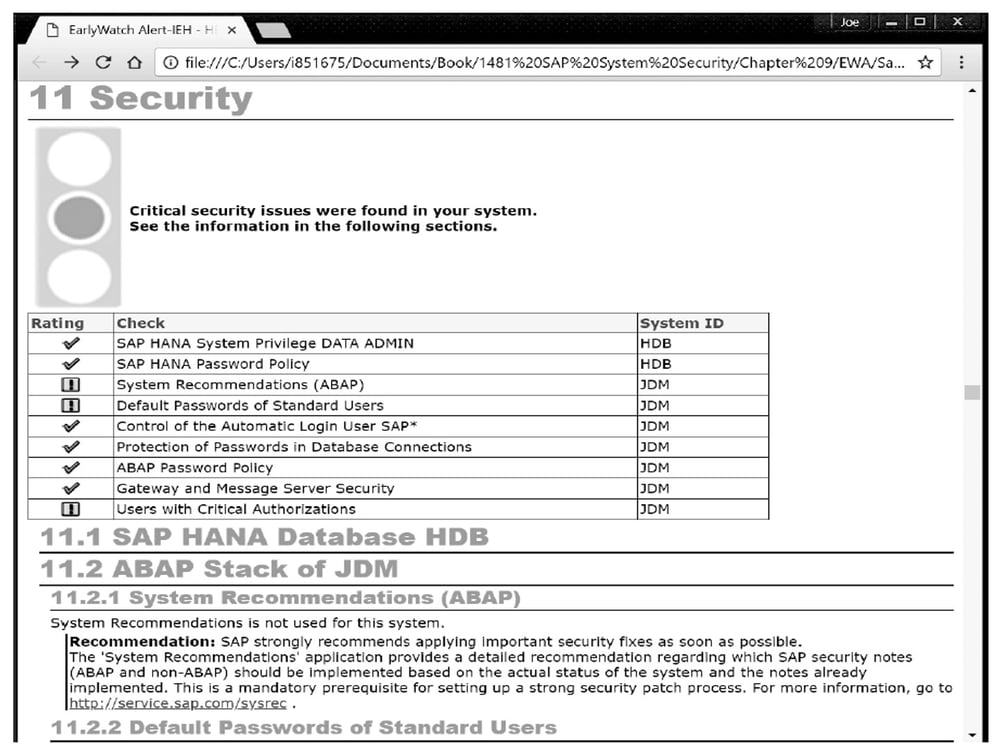
SAP EarlyWatch is a diagnostic tool that provides solution status, health, performance, growth, and security checks. Admins can set up automated SAP EarlyWatch Alert reports to see what needs attention. Additionally, these reports will call out critical SAP Notes and configurations that have yet to be implemented in a system. SAP EarlyWatch is available to any customer with an SAP Solution Manager system.
Another collaborative project with NextLabs, SAP Enterprise Digital Rights Management focuses on file protection including encryption, access rights management, and more.
SAP Enterprise Threat Detection is a tool that leverages SAP HANA to process large amounts of security events in real time, such as a cyber attack. It offers insight on how to neutralize attackers and find anomalies or damage in the system landscape following an intrusion.
SAP Fortify is an application quality management and security vulnerability testing tool that helps admins both plan security infrastructure and keep existing functionality in top shape. SAP Fortify provides businesses with a central security center, static code analyzer, and automation capability to identify and fix issues as they become known.
SAP Governance, Risk, and Compliance (SAP GRC) is a suite of solutions focused on managing multiple aspects of a business. Security components include process and access control for authorizations, audit management tools, and business integrity screening to detect fraud and screen potential business partners.
SAP Identity Management is a tool used to cover the entire identity lifecycle of a person. With this tool, admins can ensure that the people accessing data in a system are who they say they are. Similar to the SAP GRC Access Control functionality, SAP Identity Management provides password self-service capabilities to users and helps in role provisioning.
SAP Information Lifecycle Management (SAP ILM) is a tool that allows the blocking and deletion of data from an SAP system. This is especially important in instances where data privacy laws such as the General Data Protection Regulation (GDPR) and California Consumer Protection Act (CCPA) require businesses to delete customer data upon request.
With SAP ILM, admins can create defined lifecycles for data; for example, how long to keep data (retention) and where to keep it prior to archival (residence). It also allows deletion exceptions for data used in legal proceedings, permanent data destruction, and secure data storage.
SAP also offers several proactive security-related services under its MaxAttention and ActiveAttention support plans:
Because a majority of security concepts for cloud solutions, such as physical security, hardware, software platform, some applications, and more are the responsibility of SAP and not the customer, SAP has set up a public website that provides content on the ways SAP is securing their cloud products. It is called the SAP Trust Center and while not an SAP solution per se, should be mentioned in relation to SAP security.
SAP Watch List Screening helps vendors vet potential business partners to ensure they are not on watch lists published by governments and international organizations like the United Nations.
With all these tools at its disposal, SAP is confident it is compliant toward multiple financial and security-related privacy laws, including but not limited to:
Here are answers to some of the most common things SAP administrators want to know about SAP security.
Q: What is SAP security?
A: SAP security refers to the processes, tools, and best practices that protect SAP systems, data, and applications from unauthorized access, cyberattacks, and data breaches.
Q: Why is SAP security important?
A: SAP systems often store critical financial, operational, and personal data. Securing them helps prevent data loss, fraud, compliance violations, and reputational damage.
Q: What are SAP’s main security tools?
A: Key solutions include SAP Identity Management, SAP Governance, Risk, and Compliance (GRC), SAP Enterprise Threat Detection, SAP Cloud Identity Access Governance, and SAP Information Lifecycle Management.
Q: How often does SAP release security patches?
A: SAP releases patches monthly on SAP Patch Day, typically the second Tuesday of each month.
Q: How does SAP handle cloud security?
A: For cloud products, SAP manages core infrastructure security and provides customers with tools like the SAP Trust Center, encryption options, and access governance controls. Customers are still responsible for some security for cloud products.
Q: Does SAP comply with data protection laws?
A: Yes. SAP adheres to global compliance frameworks such as GDPR, HIPAA, CCPA, ISO/IEC 27001, and others, depending on the product and region.
In addition to the information laid out above, there are a handful of important SAP security terms you should also know:
Want to learn more about SAP security? Additional information can be found in the blog posts and books listed below.
Learn more SAP from our official Learning Center.
And to continue learning even more about SAP security, sign up for our weekly blog recap here: